Blockchain security firm SlowMist has highlighted five common phishing techniques crypto scammers used on victims in 2022, including malicious browser bookmarks, phony sales orders and trojan malware spread on messaging app Discord.
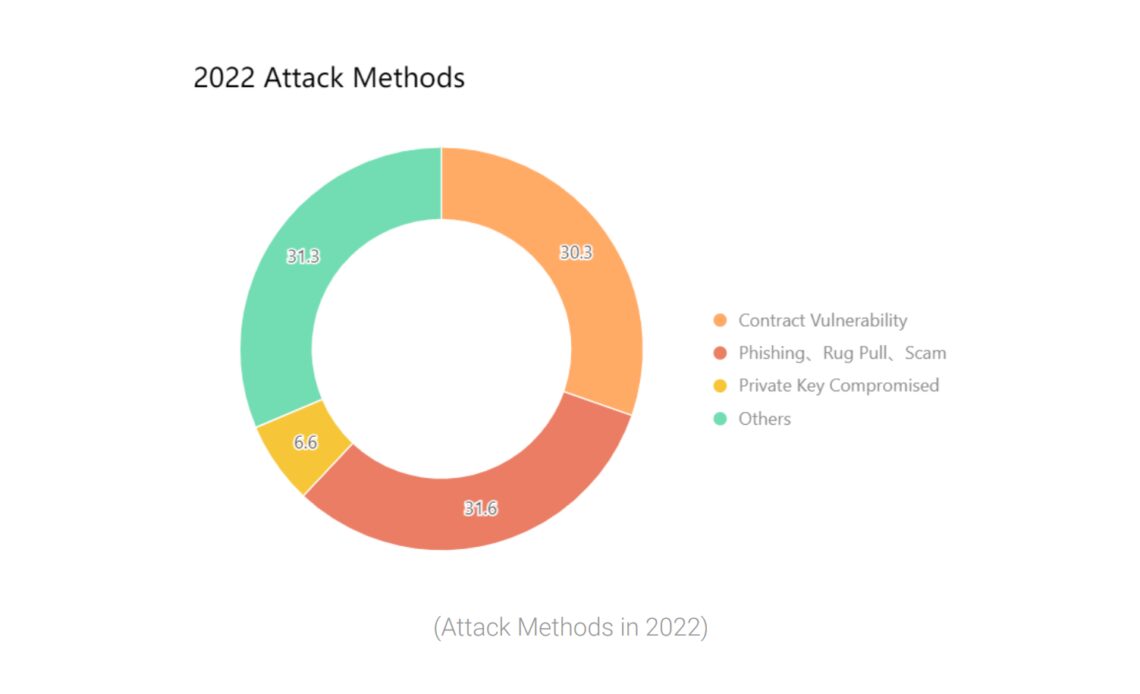
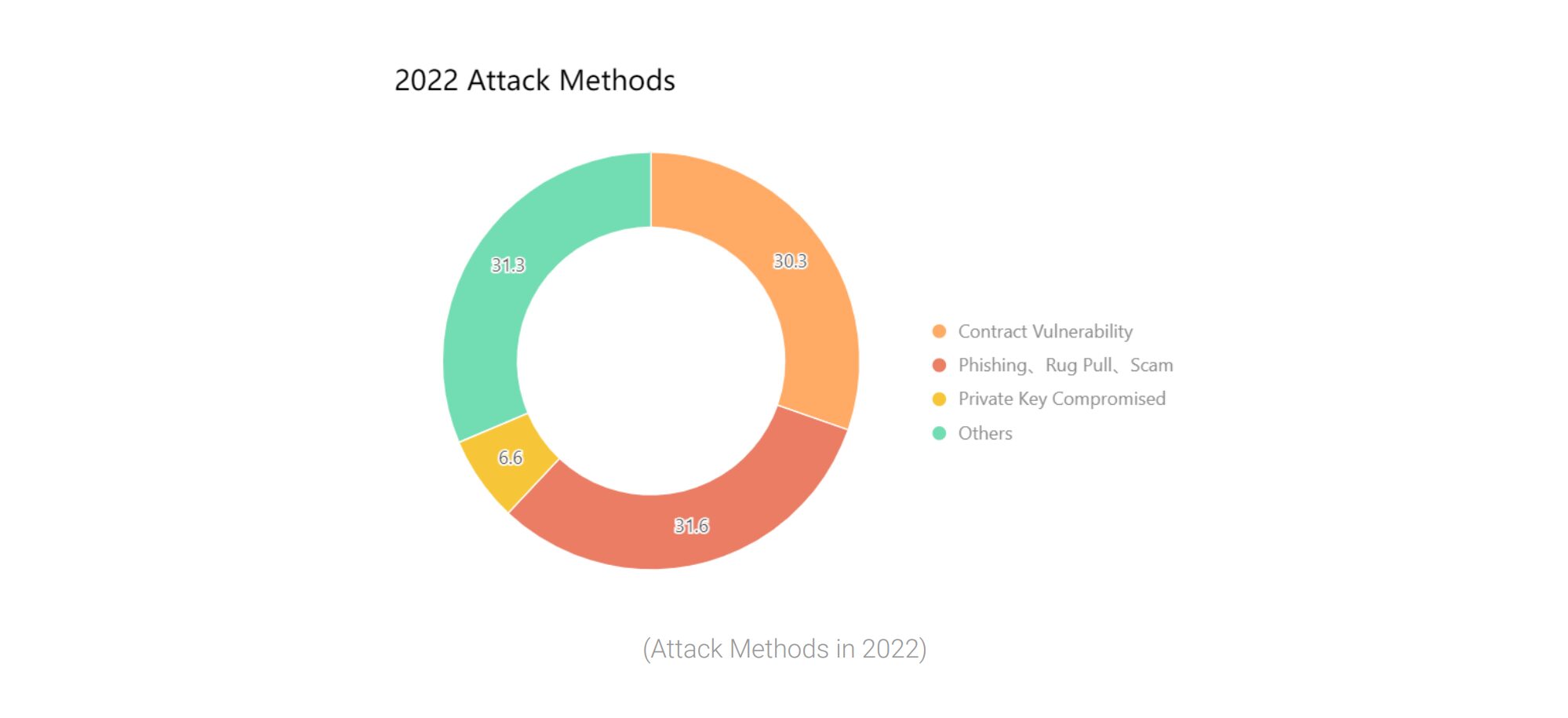
It comes after the security firm recorded a total of 303 blockchain security incidents in the year, with 31.6% of these incidents caused by phishing, rug pull or other scams, according to a Jan. 9 SlowMist blockchain security report.
Malicious browser bookmarks
One of the phishing strategies makes use of bookmark managers, a feature in most modern browsers.
SlowMist said scammers have been exploiting these to ultimately gain access to a project owner’s Discord account.
“By inserting JavaScript code into bookmarks through these phishing pages, attackers can potentially gain access to a Discord user’s information and take over the permissions of a project owner’s account,” the firm wrote.
After guiding victims to add the malicious bookmark through a phishing page, the scammer waits until the victim clicks on the bookmark while logged into Discord, which triggers the implanted JavaScript code and sends the victim’s personal information to the scammer’s Discord channel.
During this process, the scammer can steal a victim’s Discord Token (encryption of a Discord username and password) and thus gain access to their account, which allows them to post fake messages and links to more phishing scams posing as the victim.
‘Zero dollar purchase’ NFT phishing
Out of 56 major NFT security breaches, 22 of those were the result of phishing attacks, added SlowMis
One of the more popular methods used by scammers would trick their victims into signing over NFTs for practically nothing through a phony sales order.
Once the victim signs the order, the scammer can then purchase the user’s NFTs through a marketplace at a price determined by them.
“Unfortunately, it’s not possible to deauthorize a stolen signature through sites like Revoke,” the report wrote.
“However, you can deauthorize any previous pending orders that you had set up, which can help mitigate the risk of phishing attacks and prevent the attacker from using your signature.”
Trojan horse currency theft
According to SlowMist, this type of attack usually occurs through private messages on Discord where the attacker invites victims to participate in testing a new project, then sends a program in the…
Click Here to Read the Full Original Article at Cointelegraph.com News…